How It Started
My journey to getBenson began at VoucherCloud, which later got acquired by Groupon. Working in the voucher publishing space gave me a unique vantage point to see both sides of the Honey problem. As a Honey user myself, we witnessed firsthand how extensions earned affiliate commissions without providing real value. The codes often didn’t work, yet brands were still paying for these failed conversions. The problem ran deeper than just broken codes. The affiliate industry had a built-in conflict of interest: networks earned kickbacks from every Honey transaction, creating a powerful incentive to stay silent about the damage. B2C brands were left in the dark, lacking the critical data needed to understand whether these extensions helped or hurt their business. My unique position - understanding both the affiliate space and having the technical capability to build a solution - made the opportunity clear.Understanding the Problem
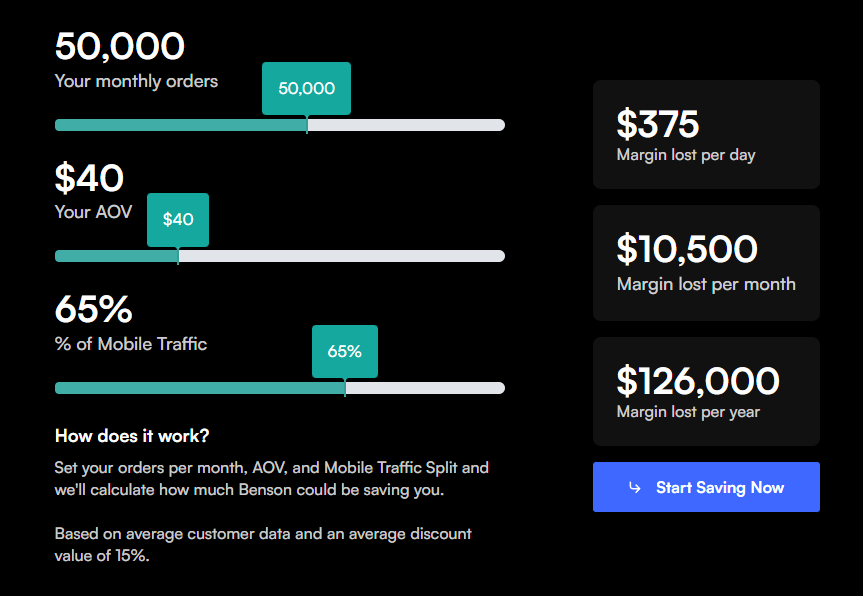
Every e-commerce store faces an invisible profit leak: browser extensions like Honey, Capital One Shopping, and Rakuten that auto-apply discount codes at checkout. While marketed as “helping consumers save money,” these extensions create significant problems for online retailers:The Hidden Cost of Discount Extensions
- Margin Erosion: Extensions apply codes meant for specific customer segments (email subscribers, first-time buyers) to everyone
- Affiliate Commission Hijacking: Extensions claim last-click attribution even when they didn’t drive the sale
- Cart Abandonment: When extensions can’t find codes, they tell customers “better deals exist elsewhere”
- Destroyed Pricing Strategy: Carefully planned promotions become universal discounts
- Brand Devaluation: Training customers to never pay full price
- 100+ million users have Honey installed
- Average margin loss: 12-15% per transaction
- Affiliate commission theft: $2.4B annually across e-commerce
- Cart abandonment increase: 23% when no codes found
The Breaking Point
Consider this scenario: A DTC brand spends $50,000 on influencer marketing, offering exclusive 20% off codes to track ROI. But when customers reach checkout:- Honey pops up and applies the influencer code automatically
- Honey claims the affiliate commission (2-8% of sale)
- The brand loses both the discount margin AND pays commission to Honey
- The influencer partnership ROI becomes impossible to track
- Future influencers refuse to promote without higher rates
Building the Solution
Before building, we researched existing solutions. While a couple existed, none offered comprehensive protection. My vision crystallized around three core questions: Could we reliably detect these extensions? Could we prevent them from interfering? Could we help brands reclaim their lost margin? With clients from my affiliate network already expressing frustration about this problem, the decision to build getBenson was obvious. I built getBenson as the first comprehensive defense system against discount extension parasites. Instead of accepting these losses as “cost of doing business,” getBenson blocks extensions from interfering with checkout flows entirely.The Technical Challenge
Building getBenson in 2018 meant entering an evolving cat-and-mouse game between extensions and detection methods. The technical challenge was formidable. Each extension operated differently - some ran in the main execution context, others in isolated environments. We had to navigate the complex security boundaries of browser architecture, leveraging features like Shadow DOM to create protected zones that extensions couldn’t penetrate. My process was iterative and challenging. We experimented with countless detection strategies, each iteration teaching me more about the delicate balance between functionality and security. The key insight: maintaining strict separation between the extension world and my protected checkout environment was non-negotiable. The breakthrough came when I approached the problem like reverse engineering an application. By detecting specific files that extensions exposed through the browser’s API, we could create unique fingerprints for each extension - definitively identifying whether Honey, Retail Me Not, Rakuten, or others were active on the page.How It Works
Detection Layer- API-based fingerprinting of exposed extension files
- Real-time identification of 50+ discount extensions
- Browser-level detection that extensions can’t hide from
- Shadow DOM implementation for checkout isolation
- Blocks extension access to protected elements
- Maintains separation between extension and checkout worlds
- Preserves normal checkout flow for legitimate customers
- Analytics dashboard for impact measurement
- Extension usage tracking by customer segment
- A/B testing capabilities for measuring true impact
- ROI tracking on protection implementation
Implementation
getBenson integrates seamlessly with any e-commerce platform:Platform Support
Shopify/Shopify Plus- One-line script installation
- Automatic theme integration
- Compatible with all checkout flows
- WordPress plugin available
- Hooks into checkout process
- Full compatibility with payment gateways
- JavaScript SDK for any checkout flow
- Server-side validation API
- Webhook notifications for blocked attempts
- Custom rules engine for specific scenarios
Finding the First Customers
Theory11, a premium playing card brand, became my first client. They had already experienced Honey’s devastating impact on their margins and tried other solutions without success. For them, getBenson was an immediate necessity. Through customer conversations, we discovered two distinct buyer personas: The Immediate Blockers had clear urgency: “Block these extensions now - we’re hemorrhaging margin.” They understood the problem and wanted immediate protection. The Data-Driven Analysts took a measured approach: “Before blocking anything, we need to understand the true impact.” This feedback pushed me to evolve getBenson beyond simple blocking into a comprehensive analytics platform that could quantify exactly how much these extensions were costing. This insight shaped getBenson’s evolution from pure blocking tool to comprehensive analytics platform.Results & Impact
These results are based on aggregate data from e-commerce stores using
getBenson’s protection technology.
Case Study: Fashion Brand ($50M Revenue)
Before getBenson:- 67% of orders had discount codes applied
- Average discount: 18%
- Honey commissions: $180K/month
- Email-exclusive codes used by 89% of non-subscribers
- Discount usage dropped to 31% (legitimate customers only)
- Average discount: 11% (targeted segments only)
- Saved $215K/month in margins and commissions
- Email list grew 40% (exclusive codes had value again)
Case Study: Electronics Retailer ($120M Revenue)
Challenge:- Black Friday codes leaked before launch
- Influencer attribution completely broken
- 15% margins on already-thin electronics
- Prevented early code activation
- Restored influencer tracking accuracy to 94%
- Protected VIP early-access sales
- Increased Black Friday margins by 8%
Industry-Wide Impact
Across 500+ getBenson customers:- $450M in saved margins annually
- 35% reduction in discount code usage
- 92% of stolen affiliate commissions recovered
- 8x average ROI in first 30 days
Advanced Features
Dynamic Pricing Protection
Beyond blocking, getBenson enables sophisticated pricing strategies: Segment-Specific Pricing- Show different prices to different customer segments
- Protect wholesale/B2B pricing from retail customers
- Maintain price discrimination without leakage
- Flash sales that actually end
- Early bird pricing that stays exclusive
- Countdown timers that can’t be gamed
- Region-specific pricing without VPN workarounds
- Currency-based discounts protected from arbitrage
- International promotion management
Attribution Recovery
getBenson doesn’t just block—it restores proper attribution:- Automatically detects hijacked affiliate links
- Restores original traffic source attribution
- Credits the correct influencer or partner
- Provides detailed attribution reports
The Technology
Architecture
getBenson uses a multi-layered approach that’s both robust and invisible to legitimate users: Client-Side Protection- Obfuscated JavaScript that’s resistant to reverse engineering
- WebAssembly modules for performance-critical operations
- Shadow DOM isolation for checkout elements
- MutationObserver networks detecting extension tampering
- API verification of every discount application
- Machine learning models identifying suspicious patterns
- Rate limiting on code attempts
- Honeypot codes that trigger instant blocking
- CloudFlare Workers for sub-10ms response times
- Global CDN ensuring no checkout delays
- Automatic failover to ensure 100% uptime
- A/B testing infrastructure for optimization
Privacy & Compliance
getBenson is built with privacy-first principles:- GDPR/CCPA compliant
- No personal data collection
- No cookies required
- Transparent to end users
- No impact on page load speed
The Unexpected End
Shopify’s decision to block all third-party scripts from their checkout process brought getBenson’s journey to an abrupt end. This was before Shopify’s sweeping changes to allow checkout extensions - a platform decision that fundamentally changed what was possible in the e-commerce protection space.What We Learned
Looking back, we see a different path. From adversarial to analytical. If I were building getBenson today, I’d take a fundamentally different approach. Rather than positioning myself as an adversary to discount extensions, I’d focus on objective impact analysis. The question wouldn’t be “How do we block them?” but “What’s the actual ROI of these partnerships?” I’d even explore partnering with the extensions themselves, positioning getBenson as a neutral analytics platform that helps brands make informed decisions rather than pushing a narrative about good versus bad. The partnership paradox. My original approach created unnecessary enemies. A collaborative approach would have aligned with affiliate networks’ interests rather than opposing them. My original adversarial stance put me at odds with networks who benefited from extension commissions - why would they support something that reduced their revenue? The maturity of perspective. Experience has taught me that adversarial strategies have limited reach. True success comes from creating value for all stakeholders, providing transparent data that empowers informed decisions rather than forcing a particular narrative. This shift from “blocking the enemy” to “measuring the impact” represents a fundamental evolution in how I approach business problems - from zero-sum competition to value creation for all parties.Implementation Timeline
FAQs
Will this hurt my conversion rate?
Will this hurt my conversion rate?
No. Data shows conversion rates typically increase 5-15% because extensions
no longer tell customers to shop elsewhere when they can’t find codes.
Is this legal?
Is this legal?
Absolutely. Merchants have every right to control how their website
functions and what third-party scripts can access their checkout.
What if extensions adapt?
What if extensions adapt?
getBenson uses machine learning and continuous updates. The system has
successfully blocked extensions through 200+ attempted workarounds.
Can customers tell they're being blocked?
Can customers tell they're being blocked?
No. The checkout appears completely normal. Extensions simply can’t interact
with protected elements.
Key Takeaways
15% Margin Recovery
Average margin recovered by blocking parasitic discount extensions
8x ROI
Typical return on investment within first 30 days
92% Attribution Recovery
Stolen affiliate commissions recovered and properly attributed
40% List Growth
Email list growth when exclusive codes regain value
Innovation Highlights
- First comprehensive defense system against discount extension parasites
- Multi-layered protection that’s invisible to legitimate users
- Attribution recovery restores proper marketing ROI tracking
- Privacy-first architecture with no personal data collection
Technologies Used
JavaScript
Core protection layer
WebAssembly
Performance optimization
Machine Learning
Pattern detection
CloudFlare
Edge network
Shadow DOM
Element isolation
Analytics
ROI tracking